Introduction
On October 31, 2024, Forbes, with support from ChainArgos, broke news that Digital Currency Group (“DCG”), a venture capital firm, earned fees generated from the laundering of funds for North Korea through DCG’s investment in crypto-asset mixer Railgun.
The 2-month long Forbes investigation revealed that DCG, which also owns the U.S.-regulated Grayscale Bitcoin Trust product, the first institutional bitcoin product, was the beneficiary of fees derived from the laundering of funds linked to North Korean hacking.
Railgun characterizes itself as a crypto-asset privacy protocol but has been used to obfuscate the proceeds of hacks, including the Harmony Bridge hack which was reported by the FBI to have been conducted by North Korea’s Lazarus Group.
This case study will show you how ChainArgos traced the fees Railgun earned from the laundering of North Korean funds to DCG, where those fees ended up, and the significant degree of manual control involved in managing, processing and distributing these fees.
In this case study, you may come across terms such as “EOA”, “proxy contract” and “implementation contract” which you may be unfamiliar with. More information about these terms can be found in the Appendix attached to the end of the case study.
What is Railgun?
Railgun claims to be a privacy protocol but operates in the same way a crypto-asset mixer does. It charges fees of 0.25% of the crypto-asset being mixed. So for instance, if the ETH token was being sent to Railgun the fees charged by Railgun would be 0.25% of the total amount of ETH running through Railgun’s service.
Following the Harmony Bridge hack by North Korea (“DPRK”) as reported by the FBI, as much as $60 million worth of hacked crypto-assets were sent to Railgun for obfuscation.
Railgun’s documentation describes the service as “100% non-custodial” and that it “has no owner.”
However, this case study will show how fees earned from the DPRK’s use of Railgun were transferred through externally owned accounts (“EOAs”) during an upgrade process, before being transferred to DCG, an investor in the Railgun protocol.
EOAs are not automated, they are addresses controlled by off-chain private keys. By sending Railgun’s fees through EOAs, Railgun “broke the decentralization” and showed that someone was running at least that part of the system manually.
A Railgun Timeline
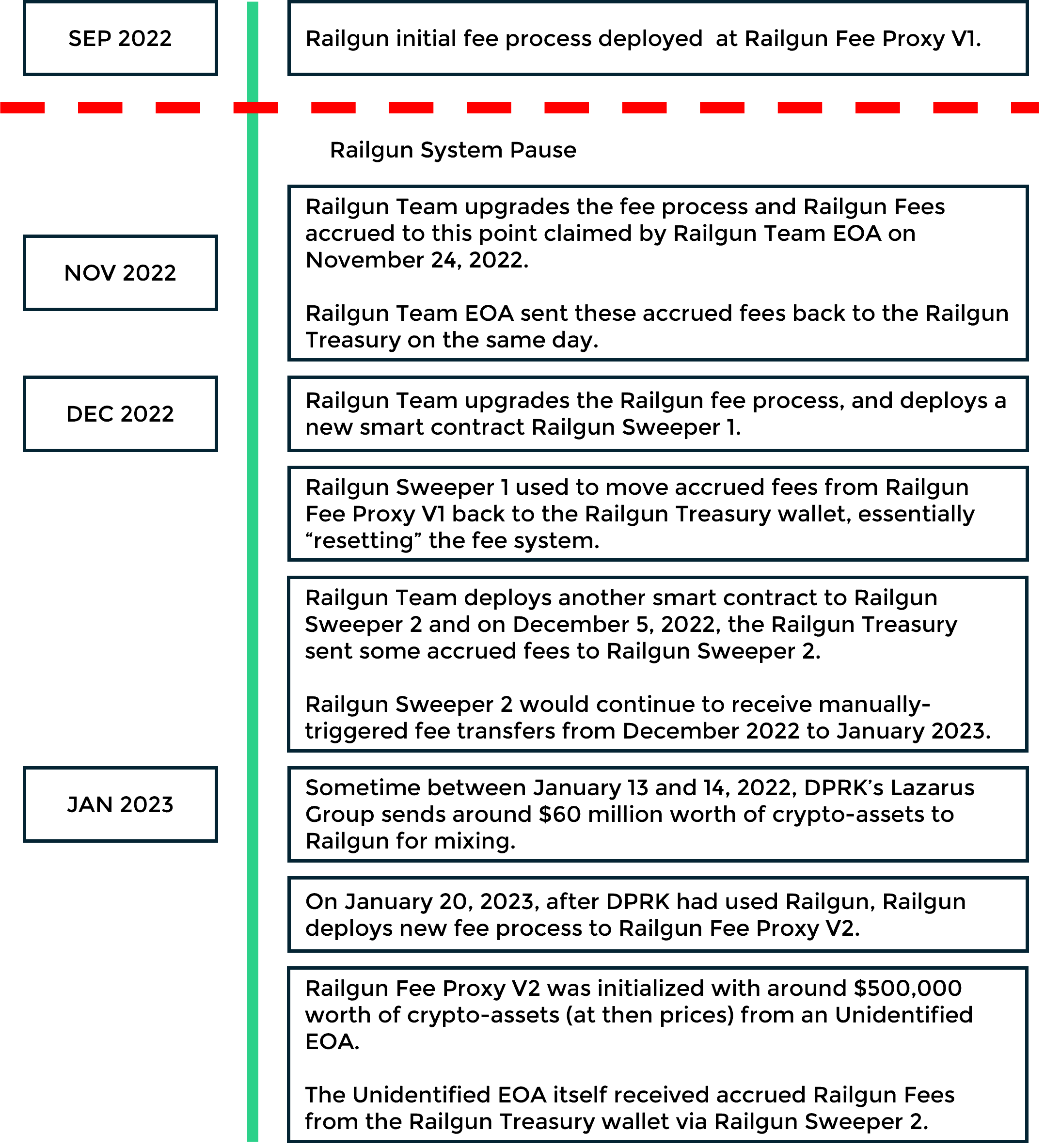
Fee Process Version 1
On September 10, 2022, Railgun’s initial fee process was deployed by the Railgun Deployer3 to the Railgun Fee Proxy V1,4 an upgradeable proxy contract.5
At around the same time a system-wide “pause” feature built into Railgun was employed to effect a series of upgrades.
Subsequently, in November 2022, Railgun deployed a series of upgrades and as part of this upgrade process, on November 24, 2022, Railgun Fees accrued to this point were claimed by the address Railgun Team EOA.6 The Railgun Team EOA then sent these fees back to the Railgun Treasury on the same day.
Already at this point the Railgun team is using EOAs rather than any automated processes to manage system fees during software upgrades.
3 0x76EB574EFF49FB64DE6f7F2854952B05B5E24624
4 0xa353bc0454931ac46fd90c8ef27f908ab9e34686
5 0x27d30e803a0ec079daa3a2e6c3590cca9f63c9d8 (Implentation Contract)
6 0xa4Dc2373d9EA3ce968427161a01c4960A90B8431
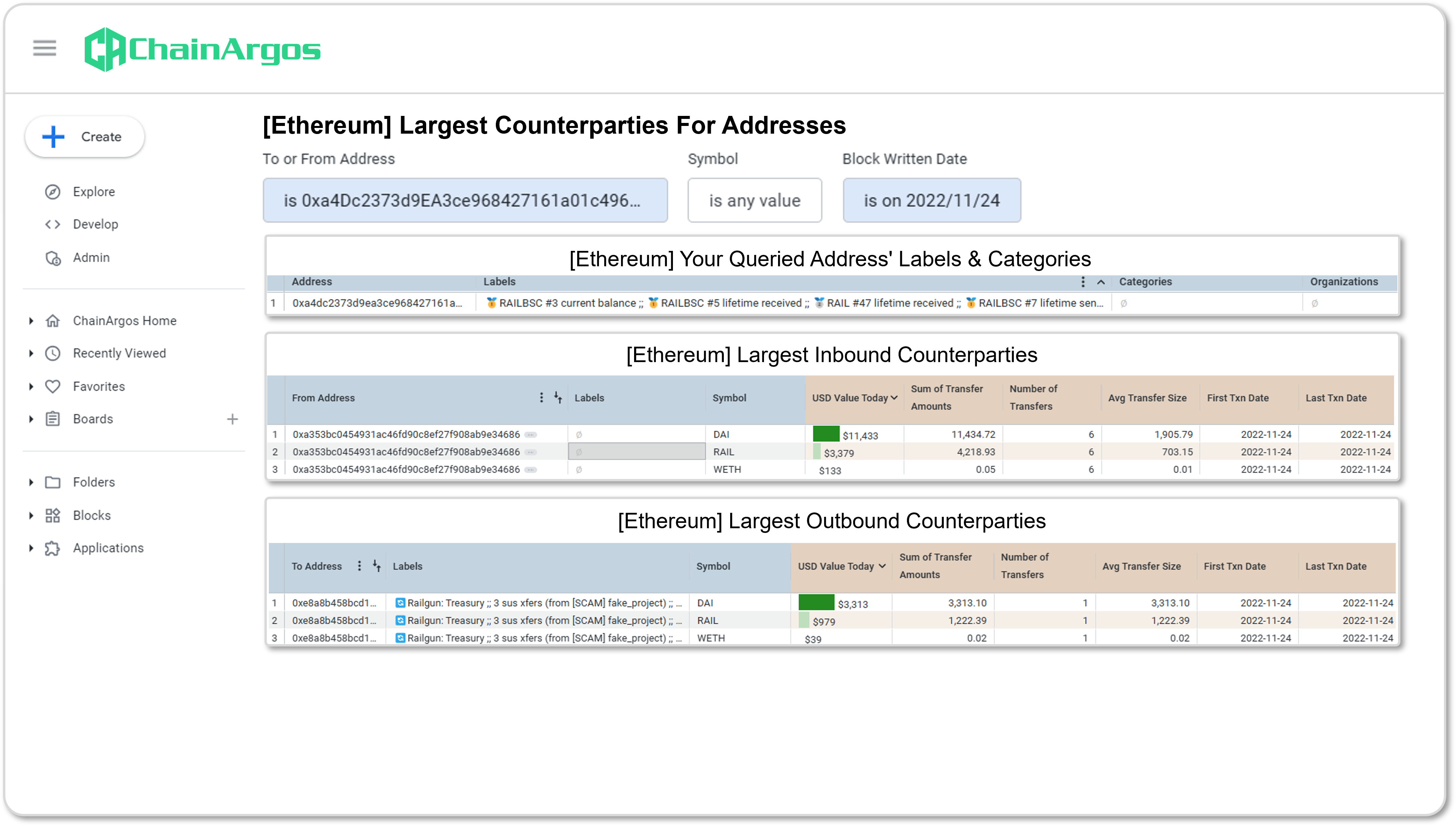
Figure 1. Largest Counterparties for Address analysis for Railgun Team EOA on November 24, 2022.
The Railgun Team EOA has been identified as associated with the Railgun Team because it received 2 million RAIL tokens during the initial distribution of RAIL tokens in July 2021, which could only have been received by contributors and developers to the Railgun protocol.
Fee Process Upgrade Begins
For whatever reason Railgun chose to upgrade its Fee Process Version 1 and on December 2, 2022 the Railgun Team deployed a new smart contract using the Railgun Deployer to Railgun Sweeper 1.7
The Railgun Team then used Railgun Sweeper 1 to move accrued fees from Railgun Fee Proxy V1 back to the Railgun Treasury wallet. This, in some sense, “reset” the fee system so a new fee process could be deployed in its place.
Separately the Railgun Team deployed Railgun Sweeper 28 and on December 5, 2022, the Railgun Treasury sent some accrued fees to Railgun Sweeper 2.
Railgun Sweeper 2 would continue to receive manually-triggered fee transfers from the Railgun Treasury throughout December 2022 and January 2023, a point we will return to later.
7 0x9b1310bdcc19d172d0092240e33209a9156c8ee2
8 0x2eca05b128bf5cbd5a73cc4bb625b51131ff119b
DPRK Use of Railgun
Between January 13th and 14th, 2023, the DPRK’s Lazarus Group sends some $60 million worth of crypto-assets to Railgun for mixing, generating a substantially larger amount of fees for the Railgun Treasury then was typical for that period, and not repeated since.
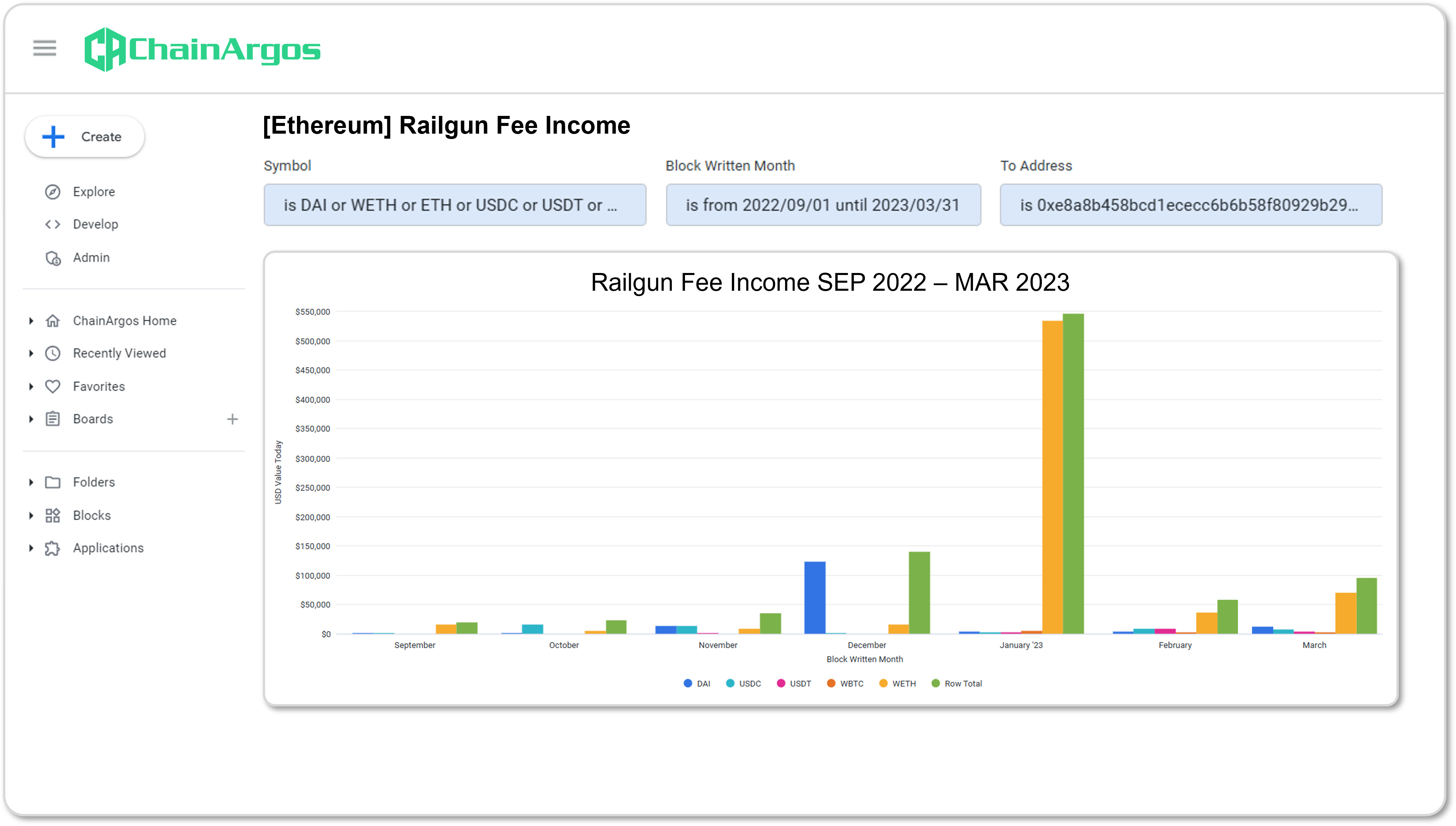
Figure 2. Railgun Fee Income between September 2022 and March 2023, with a distinct spike in fee income in January 2023, that has not been repeated since.
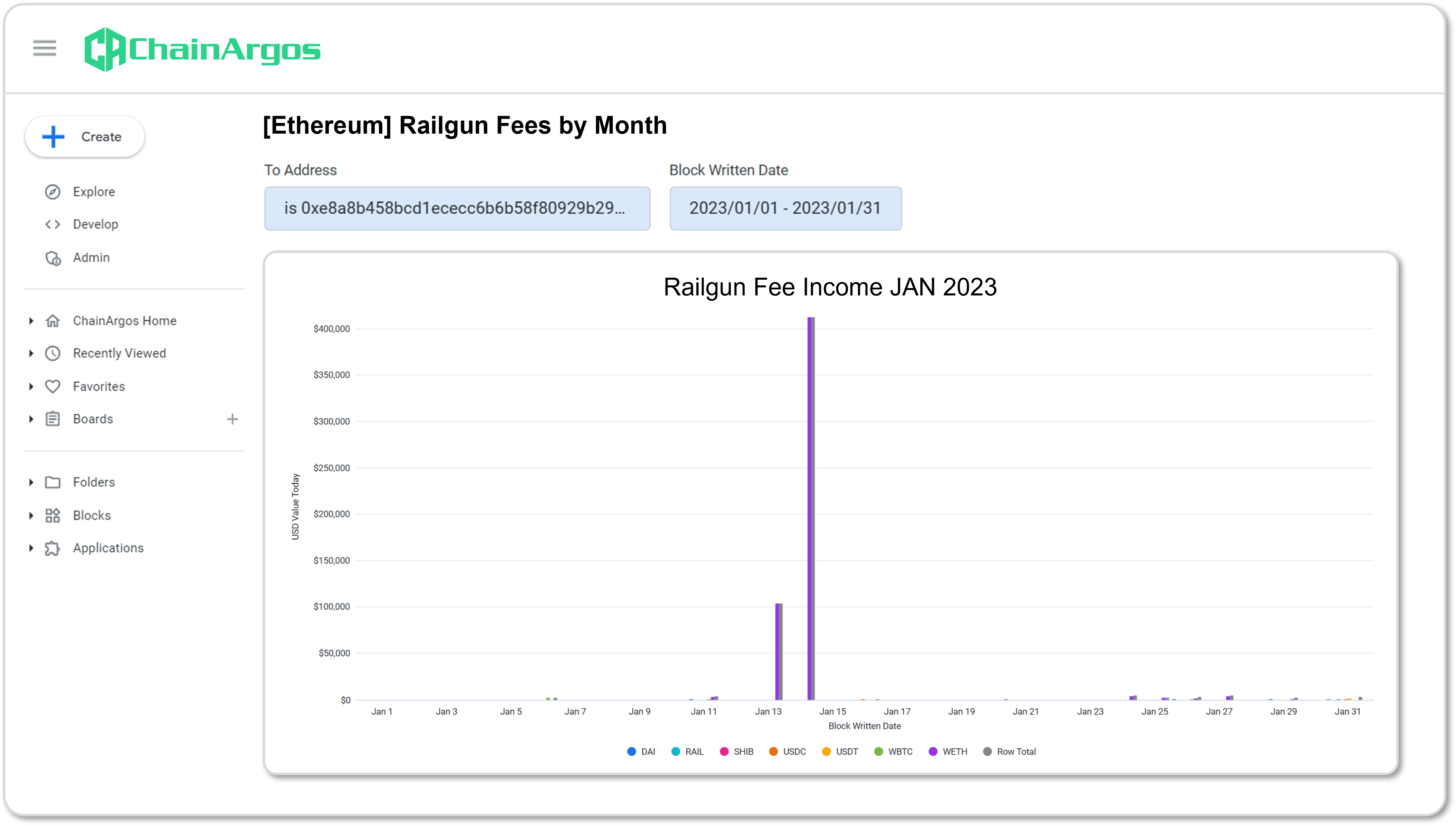
Figure 3. Railgun Fee income for the month of January, 2023 with noticeable spikes in token fees.
Between December 5, 2022 and January 18, 2023 fees from the Railgun Treasury, most of which had been generated by the DPRK’s use of Railgun, were ferried through Railgun Sweeper 2.
Fee Process Version 2
On January 20, 2023, and after the DPRK had already used Railgun, the Railgun Team deployed a new fee process to Railgun Fee Proxy V29 an upgradeable proxy contract.10
The Railgun Fee Proxy V2 was initialized with around $500,000 worth of crypto-assets on January 20, 2023, from an Unidentified EOA11 via three transactions.
The Unidentified EOA itself had received accrued Railgun Fees from the Railgun Treasury Wallet, via Railgun Sweeper 2, on January 20, 2023 – these were fees derived from the use of Railgun by the DPRK.
Railgun Sweeper 2 was deployed by the Railgun Team and used to relay fees since December 5, 2022.
Significantly, some $382,660 worth of the stablecoin DAI was sent from the Unidentified EOA to the Railgun Fee Proxy V2.
9 0xa02782ce1bf85f56f8cc7c0e66e61299ac75c86f
10 0xaF51CD5f71Ed88D6d1F65b575f1a8Ce3a78eC42b (Implementation Contract)
11 0xA140265ac0a55C49AD4373CDc92Bfa8baF41f459
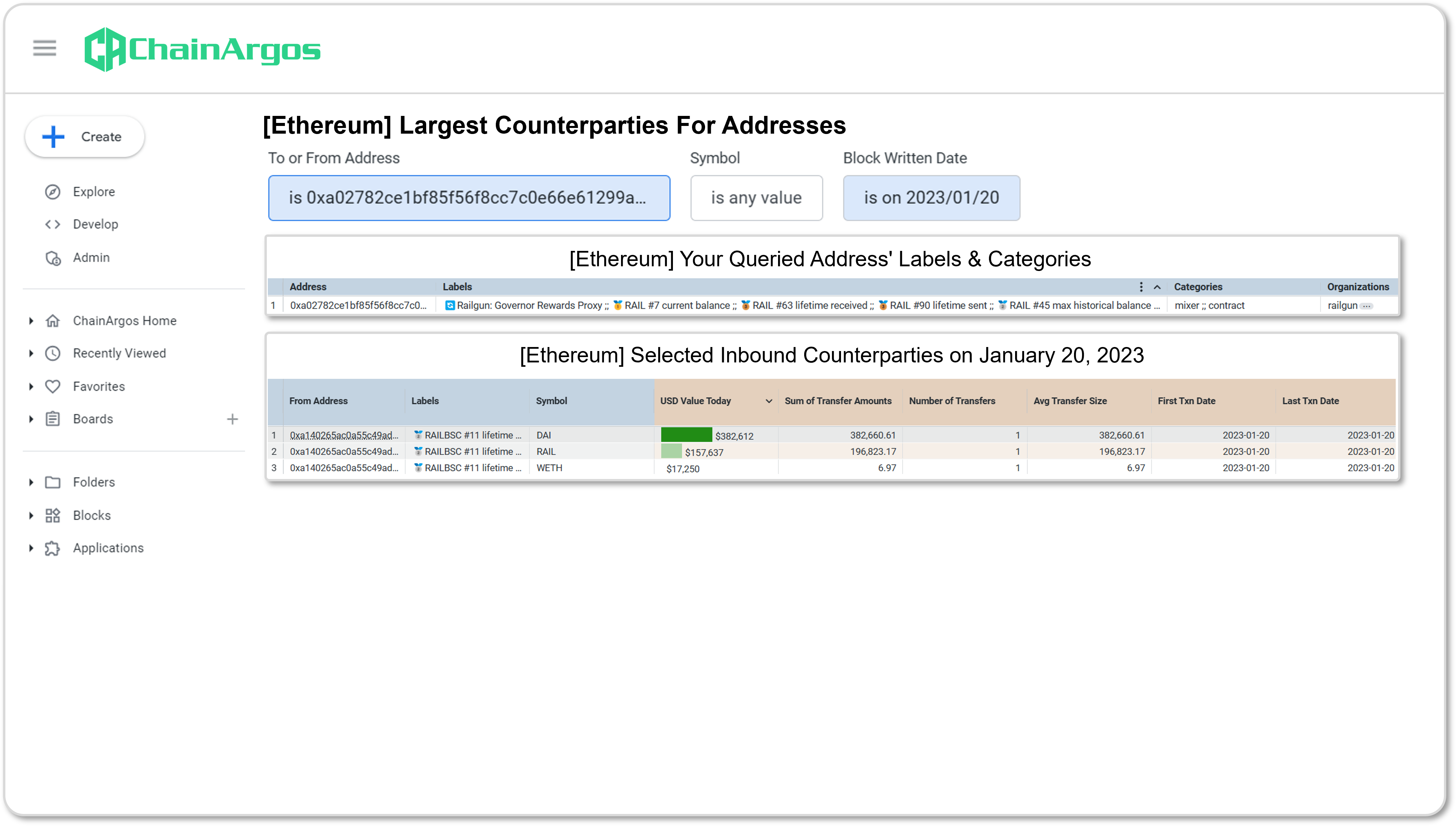
Figure 4. Railgun Fee Proxy V2 initialized by an Unidentified EOA via three transactions on January 20, 2023.
In addition, the Unidentified EOA was itself initially funded by the crypto-asset exchange SideShift, which does not require users to provide any identify verification. This strongly suggests that whoever was operating the Unidentified EOA did not want to be associated with these series of transfers, given their connection with the DPRK.
The use of the Unidentified EOA and Railgun Sweeper 2 were integral to Railgun’s fee upgrade process because this allowed the Railgun Team to move historically accrued fees from the old version of the fee system to the new one.
How are Railgun’s fees claimed?
As with many blockchain-based protocols, fees in Railgun are “claimed” by the recipient rather than being proactively sent from the protocol. This is primarily the case because someone needs to pay transaction costs for all blockchain transactions and protocols, again generally, do not subsidize this for their users or investors.
Because sending out fees in and of itself attracts blockchain network transaction fees, Railgun apportions, segregates, and assigns fees due to investors in the protocol and beneficiaries can claim them at any time they choose.
Railgun fees are generated by the protocol’s provision of mixing services, and investors who have “staked” Railgun tokens (locked them in the Railgun protocol to earn fees) receive a portion of such fees in proportion to the amount of Railgun tokens staked.
But instead of making these fees available for distribution constantly, Railgun transfers 2% of accumulated fees to its rewards process every 2 weeks, which means that every claim by an investor for fees necessarily includes fees from prior transactions.
Digital Currency Group (“DCG”), a U.S.-registered venture capital company that also owns the Grayscale Bitcoin Trust product, was one of the largest investors in Railgun.
DCG made its claim for its share of Railgun fees only in June 2023, almost five months after the DPRK’s use of Railgun in January of that same year.
There are a variety of reasons why an investor may wait to claim fees they are due, including saving on transaction fees by allowing fees to accumulate, before claiming them in one large tranche.
It is also possible that investors who were aware of the DPRK’s use of Railgun to launder funds wanted to distance themselves from fees generated through such activities.
Where do DCG’s Railgun fees end up?
Forbes details how the address 0xFED429FB7d243380B25bC11B10561D5A27f42D8E receives DCG’s share of Railgun fees.
What’s interesting is that although the ETH and DAI tokens that DCG earned from Railgun’s fee distribution were sent to Coinbase Prime Custody (“Coinbase”), RAIL tokens, were sent to a multi-sig wallet12 that appears linked to DCG.
It is unclear whether Coinbase performed any analysis of the source of DCG’s ETH and DAI tokens, nor is it clear whether Coinbase would have rejected those tokens had it known they were fees derived from the DPRK’s use of Railgun to launder funds.
Regardless, the ETH and DAI tokens that were generated from the DPRK’s use of Railgun are, given the fee structure of Railgun, directly linked to the DPRK and eventually entered Coinbase’s custody.
12 0x6b3B9EC869F8fAb3C21b15b8E8663Dfa2941F2d0
Did DCG participate in “management”?
Unlike a corporation, Railgun, similar to many other so-called decentralized protocols, operates through a decentralized autonomous organization (“DAO”) which allows holders of Railgun’s RAIL token to vote on various proposals.
At the time this case study was prepared, DCG actively voted on two Railgun DAO proposals, both of which passed.
It is unclear if DCG’s voting in these proposals is sufficient to constitute “management” in the traditional sense, especially given Railgun has an identifiable team that also appears involved in parts of the protocol’s operation.
DAOs are a relatively new legal construct and there is limited precedent to go on at the present time.
Voting on proposals is not the same as management, but given that many DAOs hold themselves out as not having a centralized management team, an argument could be made that voters in the DAO are therefore acting as de facto managers in a common enterprise.
Could this have been prevented?
In May 2023, Railgun partnered with Chainway Labs to create Railgun’s Private Proofs of Innocence (“PPI”) to prevent the automated portions of Railgun’s system from accepting funds from OFAC-blacklisted addresses and other questionable sources.
Software code for Railgun’s PPI appears in Railgun’s public code repository only from November 2023, well after the DPRK had used Railgun’s services.
As all of the activities discussed here predate the introduction of PPI by months at the very least, Railgun’s PPI process could not possibly have stopped these DPRK flows.
Furthermore, PPI applies only to the automated portions of Railgun’s fee system, but as demonstrated by the various fee upgrades, fees accumulated prior to upgrades were routinely transferred manually to EOAs outside the supervision of Railgun’s PPI.
EOAs are not automated or constrained in any way. Whoever holds the keys can effect any transactions they wish.
The PPI system requires Railgun users to provide cryptographic proof that their crypto-assets do not originate from sanctioned wallets. The thinking is that legitimate users of Railgun would provide such proofs whereas illicit users are unlikely to do so.
But given how bad actors can easily spin up fresh unsanctioned wallet address, and add layers of transactions between the illicit activity and the wallet address which eventually uses Railgun’s services, it appears there may be trivial methods to overcome PPI.
Prior to the DPRK’s use of Railgun, the so-called privacy protocol was also not a very active obfuscation platform. This is reflected in the fees generated from the provision of its mixing services.
The sudden spike in inflows to Railgun in January 2023 should have drawn attention from the Railgun Team, especially given it was a significant change in flows.
Instead, the Railgun Team elected to deny the DPRK had used their services and opted to handle the fees generated from the DPRK’s use of Railgun in manually-controlled EOAs over the course of their various upgrades to the Railgun fee system.

